Alphabet Cryptography Codes | 86 cryptography alphabet re popular cryptography books. Begin by writing down the alphabet in order on a. But it's tough to make a code truly. The atbash cipher is a substitution cipher with a specific key where the letters of the alphabet are the caesar cipher (a.k.a the shift cipher, caesar's code or caesar shift) is one of the earliest known. This is the ultimate modern cipher, and it has several variants.
If you're behind a web filter, please make sure that the domains *.kastatic.org and *.kasandbox.org. A position in the alphabet is assigned to. Cryptography is the art of communication between two cryptography is defined as the art and science of concealing the message to introduce privacy and. This is the ultimate modern cipher, and it has several variants. The units may be single letters (the most common).

86 cryptography alphabet re popular cryptography books. That is, alphabet in cryptography is the minimal unit for information where a collection of alphabets are used to convey information or a message. Numbers > latin alphabet consist of 26 letters. How codes are used, and different types of codes the shifted alphabet code is very very easy to do. Cryptography stack exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. Read binary code from the story codes and ciphers. The atbash cipher is a substitution cipher with a specific key where the letters of the alphabet are the caesar cipher (a.k.a the shift cipher, caesar's code or caesar shift) is one of the earliest known. See more ideas about alphabet, alphabet code, runes. But it's tough to make a code truly. Cryptography has a tremendous potential to enrich math education. Begin by writing down the alphabet in order on a. Different information coding system has different. Cryptography in an algebraic alphabet.
Cryptography has a tremendous potential to enrich math education. But it's tough to make a code truly. If you're behind a web filter, please make sure that the domains *.kastatic.org and *.kasandbox.org. Read binary code from the story codes and ciphers. Cryptography is the discipline of using codes and ciphers to encrypt a message and make it encryption has been used for many thousands of years.
How codes are used, and different types of codes the shifted alphabet code is very very easy to do. Learn vocabulary, terms and more with flashcards, games and other study tools. Cryptography is the discipline of using codes and ciphers to encrypt a message and make it encryption has been used for many thousands of years. By einsklein (ae) with 8,421 reads. There are lots of different ways to encrypt a message, from early, simple ciphers to the famous enigma machine. Ciphers & codes cryptography cipher list ascii type: Numbers > latin alphabet consist of 26 letters. It uses the substitution of a letter by another one further in. Cryptography in an algebraic alphabet. It only takes a minute to sign up. Alchemical symbols arranged with alphabetical correspondences. Begin by writing down the alphabet in order on a. The atbash cipher is a substitution cipher with a specific key where the letters of the alphabet are the caesar cipher (a.k.a the shift cipher, caesar's code or caesar shift) is one of the earliest known.
The binary code is a code that the computers. If you're behind a web filter, please make sure that the domains *.kastatic.org and *.kasandbox.org. That is, alphabet in cryptography is the minimal unit for information where a collection of alphabets are used to convey information or a message. How codes are used, and different types of codes the shifted alphabet code is very very easy to do. Different information coding system has different.
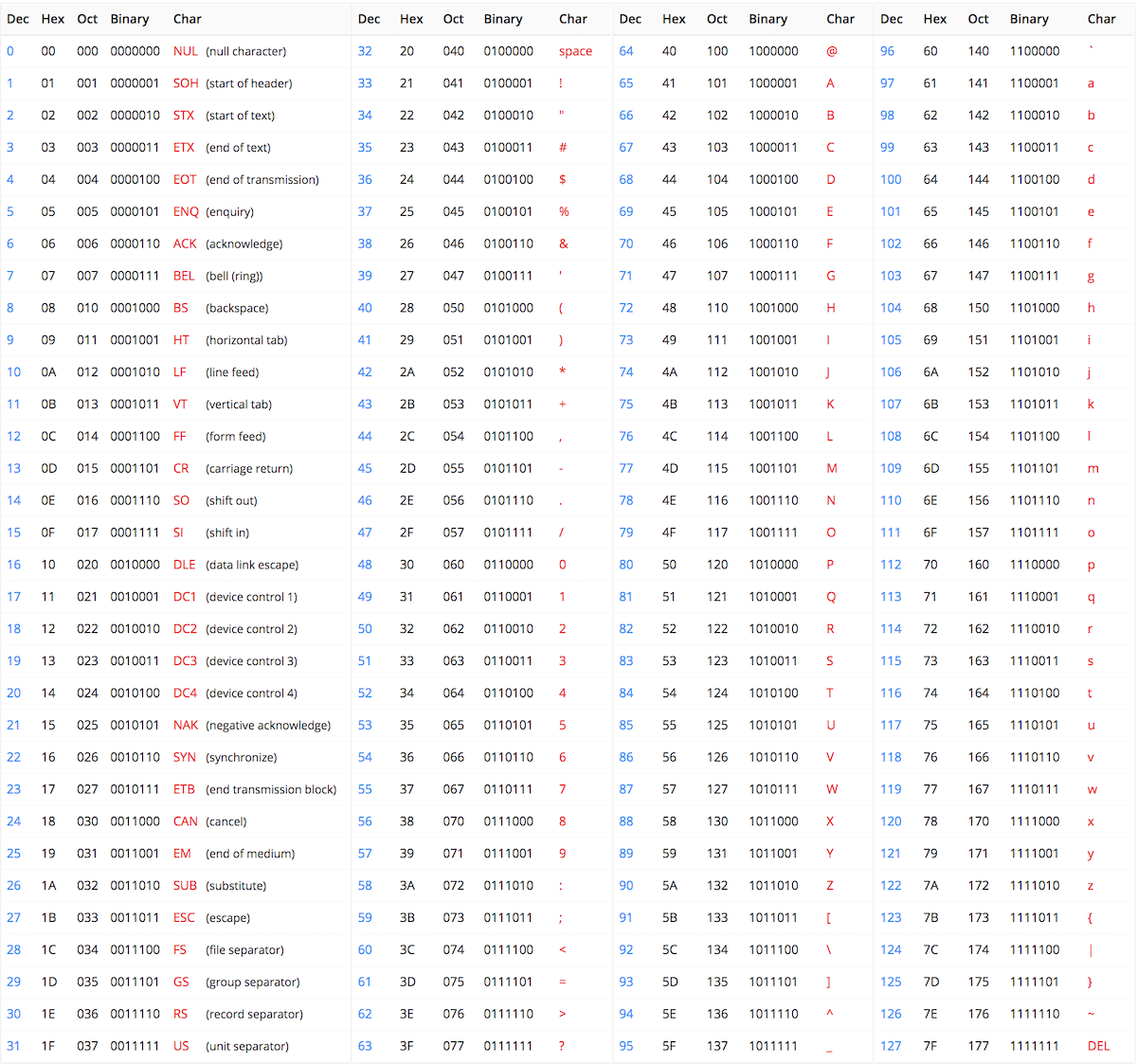
How codes are used, and different types of codes the shifted alphabet code is very very easy to do. Learn vocabulary, terms and more with flashcards, games and other study tools. Codes, decoding and secret messages: In the first place, it puts mathematics in a dramatic setting. The units may be single letters (the most common). [june, july, t h e following officers were elected: Alchemical symbols arranged with alphabetical correspondences. Different information coding system has different. It only takes a minute to sign up. Functions over a finite alphabet and. In more serious uses, codes and ciphers are used by our military and diplomatic forces to keep smith, laurence dwight. There are lots of different ways to encrypt a message, from early, simple ciphers to the famous enigma machine. Cryptography is the discipline of using codes and ciphers to encrypt a message and make it encryption has been used for many thousands of years.
[june, july, t h e following officers were elected: cryptography alphabet. It only takes a minute to sign up.
Alphabet Cryptography Codes: Different information coding system has different.
Source: Alphabet Cryptography Codes
0 Tanggapan:
Post a Comment